
Llano Phone Stand Tablet Stand Desktop Stand Foldable And Portable Adjustable Height 360 Rotation Suitable For 4 12 Inches Phones And Tablets | Save Money On Temu | Temu
![IP Routing EIGRP Configuration Guide, Cisco IOS Release 12.2SX - Configuring EIGRP [Cisco IOS Software Releases 12.2 SX] - Cisco IP Routing EIGRP Configuration Guide, Cisco IOS Release 12.2SX - Configuring EIGRP [Cisco IOS Software Releases 12.2 SX] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/000001-100000/45501-50000/46001-46500/46095.ps/_jcr_content/renditions/46095.jpg)
IP Routing EIGRP Configuration Guide, Cisco IOS Release 12.2SX - Configuring EIGRP [Cisco IOS Software Releases 12.2 SX] - Cisco

EIGRP – Quick review of EIGRP Named Mode, walk through of “Named Mode” EIGRP Configuration with Authentication across the entire EIGRP AS 100 Domain! – The DEVNET GRIND!
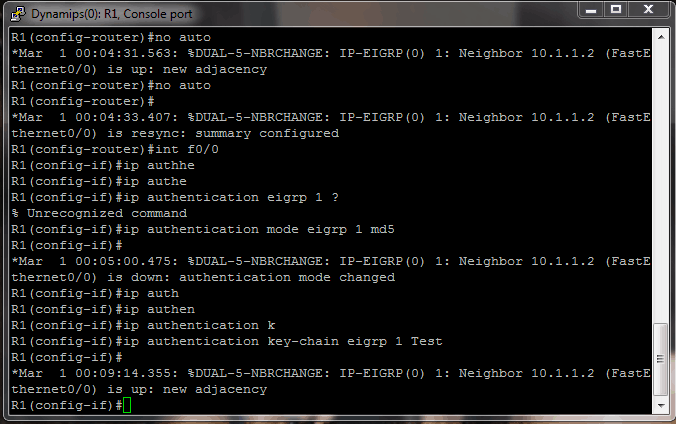
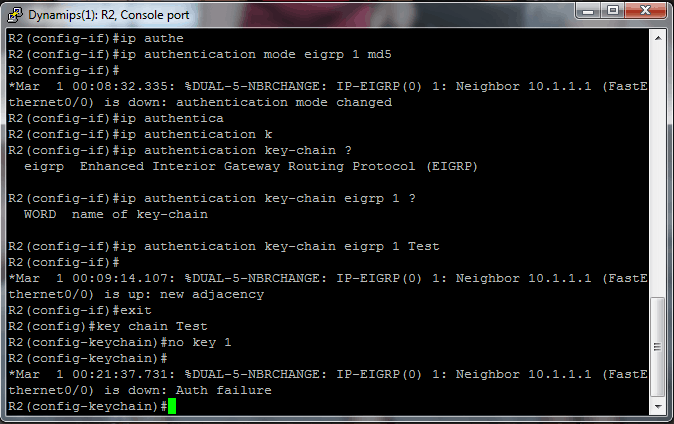
Cisco EIGRP authentication – what is the key? | Interface Technical Training | Interface Technical Training

EIGRP: Named mode, a whole new type of EIGRP mode, with all new configurations and explanations including “address-family”s! – The DEVNET GRIND!

Configure Cisco Router for Remote Access IPsec VPN Connections | Aaron Walrath - Another IT Guy's Meanderings













![Cisco OER Master Controller Engine GUI [Support] - Cisco Systems Cisco OER Master Controller Engine GUI [Support] - Cisco Systems](https://www.cisco.com/en/US/i/100001-200000/110001-120000/116001-117000/116687.jpg)

